Hackers infect 500,000 consumer routers all over the world with malware
https://ift.tt/2IJoCfB

Hackers, possibly working for an advanced nation, have infected more than 500,000 home and small-office routers around the world with malware that can be used to collect communications, launch attacks on others, and permanently destroy the devices with a single command, researchers at Cisco warned Wednesday.
VPNFilter—as the modular, multi-stage malware has been dubbed—works on consumer-grade routers made by Linksys, MikroTik, Netgear, TP-Link, and on network-attached storage devices from QNAP, Cisco researchers said in an advisory. It’s one of the few pieces of Internet-of-things malware that can survive a reboot. Infections in at least 54 countries have been slowly building since at least 2016, and Cisco researchers have been monitoring them for several months. The attacks drastically ramped up during the past three weeks, including two major assaults on devices located in Ukraine. The spike, combined with the advanced capabilities of the malware, prompted Cisco to release Wednesday’s report before the research is completed.
Expansive platform serving multiple needs
“We assess with high confidence that this malware is used to create an expansive, hard-to-attribute infrastructure that can be used to serve multiple operational needs of the threat actor,” Cisco researcher William Largent wrote. “Since the affected devices are legitimately owned by businesses or individuals, malicious activity conducted from infected devices could be mistakenly attributed to those who were actually victims of the actor. The capabilities built into the various stages and plugins of the malware are extremely versatile and would enable the actor to take advantage of devices in multiple ways.”
Sniffers included with VPNFilter collect login credentials and possibly supervisory control and data acquisition traffic. The malware also makes it possible for the attackers to obfuscate themselves by using the devices as nondescript points for connecting to final targets. The researchers also said they uncovered evidence that at least some of the malware includes a command to permanently disable the device, a capability that would allow the attackers to disable Internet access for hundreds of thousands of people worldwide or in a focused region, depending on a particular objective.
“In most cases, this action is unrecoverable by most victims, requiring technical capabilities, know-how, or tools that no consumer should be expected to have,” Cisco’s report stated. “We are deeply concerned about this capability, and it is one of the driving reasons we have been quietly researching this threat over the past few months.”
Cisco’s report comes five weeks after the US Department of Homeland Security, FBI, and the UK’s National Cyber Security Center jointly warned that hackers working on behalf of the Russian government are compromising large numbers of routers, switches, and other network devices belonging to governments, businesses, and critical-infrastructure providers. Cisco’s report doesn’t explicitly name Russia, but it does say that VPNFilter contains a broken function involving the RC4 encryption cipher that’s identical to one found in malware known as BlackEnergy. BlackEnergy has been used in a variety of attacks tied to the Russian government, including one in December 2016 that caused a power outage in Ukraine.
BlackEnergy, however, is believed to have been repurposed by other attack groups, so on its own, the code overlap isn’t proof VPNFilter was developed by the Russian government. Wednesday’s report provided no further attribution to the attackers other than say they used the IP address 46.151.209.33 and the domains toknowall[.]com and api.ipify[.]org.
Advanced group
There’s little doubt that whoever developed VPNFilter is an advanced group. Stage 1 infects devices running Busybox- and Linux-based firmware and is compiled for several CPU architectures. The primary purpose is to locate an attacker-controlled server on the Internet to receive a more fully featured second stage. Stage 1 locates the server by downloading an image from Photobucket.com and extracting an IP address from six integer values used for GPS latitude and longitude stored in the EXIF field. In the event the Photobucket download fails, stage 1 will try to download the image from toknowall[.]com.
If that fails, stage 1 opens a “listener” that waits for a specific trigger packet from the attackers. The listener checks its public IP from api.ipify[.]org and stores it for later use. This is the stage that persists even after the infected device is restarted.
Cisco researchers described stage 2 as a “workhorse intelligence-collection platform” that performs file collection, command execution, data exfiltration and device management. Some versions of stage 2 also possess a self-destruct capability that works by overwriting a critical portion of the device firmware and then rebooting, a process that renders the device unusable. Cisco researchers believe that, even without the built-in kill command, the attackers can use stage 2 to manually destroy devices.
Stage 3 contains at least two plugin modules. One is a packet sniffer for collecting traffic that passes through the device. Intercepted traffic includes website credentials and Modbus SCADA protocols. A second module allows stage 2 to communicate over the Tor privacy service. Wednesday’s report said Cisco researchers believe stage 3 contains other plugins that have yet to be discovered.
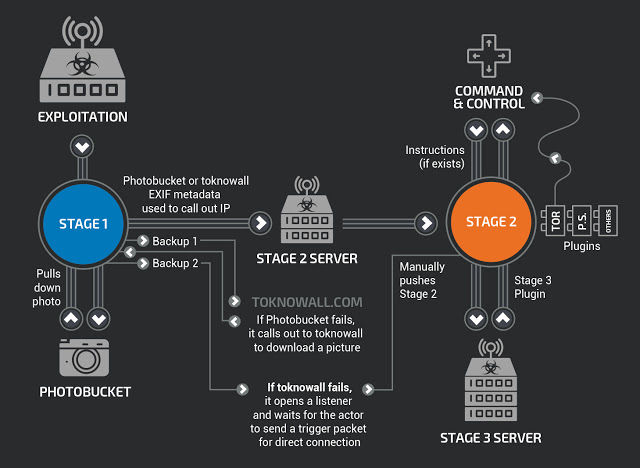
The three stages of VPNFilter
Cisco
Hard to protect
Wednesday’s report is concerning because routers and NAS devices typically receive no antivirus or firewall protection and are directly connected to the Internet. While the researchers still don’t know precisely how the devices are getting infected, almost all those targeted have known public exploits or default credentials that make compromise straightforward. Antivirus provider Symantec issued its own advisory Wednesday that identified the targeted devices as:
- Linksys E1200
- Linksys E2500
- Linksys WRVS4400N
- Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
- Netgear DGN2200
- Netgear R6400
- Netgear R7000
- Netgear R8000
- Netgear WNR1000
- Netgear WNR2000
- QNAP TS251
- QNAP TS439 Pro
- Other QNAP NAS devices running QTS software
- TP-Link R600VPN
Both Cisco and Symantec are advising users of any of these devices to do a factory reset, a process that typically involves holding down a button in the back for five to 10 seconds. Unfortunately, these resets wipe all configuration settings stored in the device, so users will have to reenter the settings once the device restarts. At a minimum, Symantec said, users of these devices should reboot their devices. That will stop stages 2 and 3 from running, at least until stage 1 manages to reinstall them.
Users should also change all default passwords, be sure their devices are running the latest firmware, and, whenever possible, disable remote administration. Cisco researchers urged both consumers and businesses to take the threat of VPNFilter seriously.
“While the threat to IoT devices is nothing new, the fact that these devices are being used by advanced nation-state actors to conduct cyber operations, which could potentially result in the destruction of the device, has greatly increased the urgency of dealing with this issue,” they wrote. “We call on the entire security community to join us in aggressively countering this threat.”
Tech
via Ars Technica https://arstechnica.com
May 23, 2018 at 03:18PM
